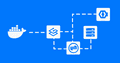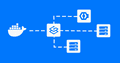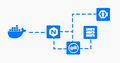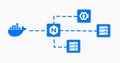
VirtualBox Raw Disk Access & Booting from Real Partitions
September 22, 2023
For a variety of reasons, device and software manufacturers implement various levels of restrictions to prevent users from accessing saved WiFi keys. On Android (depending on your device model/software) you may be able to access the key for an individual access point, or share this information via a QR code. This data may even be included when using Google to backup/restore your Android device…
Docker is not inherently secure by default, especially since the daemon-container architecture runs as root by default. There are many ways you can significantly limit the consequences of an attack should one compromise your system via your services/containers. This post served as my guide when getting started with self-hosting. This list is in no way comprehensive, so let me know in the comments…
Introduction to VirtualBox VirtualBox is a widely used virtualization software that was acquired by Oracle in 2010. It enables users to create and run software-based emulations of a physical computer system (virtual machines) on their computers. This allows users to run multiple operating systems simultaneously without the need for separate physical hardware. Whether you're a developer or simply…
To increase security you should be using rootless Docker where you can. As written by Jake Howard: Docker containers, and containers as a whole, are really just a regular program wrapped in some extra protections provided by the kernel (namely cgroups etc) to create isolation, and other interesting features. Unlike VMs, containers run closer to the host operating system, so close they use the same…
Android Auto for Phone Screens was a feature provided by Google for Android smartphones. It allowed users to access a simplified version of the Android Auto interface directly on their phone's screen, without the need for a compatible car infotainment system. In essence, it allowed you to use Android Auto's features and interface while using your phone as a standalone device in your car. You could…
Emails are an important part of many of our lives - both personally and professionally. Staying on top of your inbox can be a daunting task. My matter how hard I try, inevitably my Gmail begins overflowing with countless unread messages. In this guide we will explore how Python can be utilized to effortlessly sort through your inbox, allowing you to regain control. Note: The purpose of this post…
This guide is the second part in a multi-part series of guides: Self-hosting SSO (Part 1): Keycloak [with Nginx | with Traefik] Self-hosting SSO (Part 2): Reverse Proxy Auth with OAuth2 Proxy [with Nginx | with Traefik] *here* Self-hosting SSO (Part 3): Keycloak + LDAP Why do we need Reverse Proxy Auth? In the first part of this guide, we covered setting up Keycloak. This gives us single sign-on…
This guide is the first part in a multi-part series of guides: Self-hosting SSO (Part 1): Keycloak [with Nginx | with Traefik] *here* Self-hosting SSO (Part 2): Reverse Proxy Auth with OAuth2 Proxy [with Nginx | with Traefik] Self-hosting SSO (Part 3): Keycloak + LDAP The dream There are plenty of great services to self-host, including Nextcloud, and Tandoor Recipes. If you've ever tried self…
This guide is the third part in a multi-part series of guides: Self-hosting SSO (Part 1): Keycloak [with Nginx | with Traefik] Self-hosting SSO (Part 2): Reverse Proxy Auth with OAuth2 Proxy [with Nginx | with Traefik] Self-hosting SSO (Part 3): Keycloak + LDAP *here* What is LDAP? LDAP is an acronym for "Lightweight Directory Access Protocol". LDAP is a software protocol that is used to enable…
This guide is the second part in a multi-part series of guides: Self-hosting SSO (Part 1): Keycloak [with Nginx | with Traefik] Self-hosting SSO (Part 2): Reverse Proxy Auth with OAuth2 Proxy [with Nginx | with Traefik] *here* Self-hosting SSO (Part 3): Keycloak + LDAP Why do we need Reverse Proxy Auth? In the first part of this guide, we covered setting up Keycloak. This gives us single sign-on…
This guide is the first part in a multi-part series of guides: Self-hosting SSO (Part 1): Keycloak [with Nginx | with Traefik] *here* Self-hosting SSO (Part 2): Reverse Proxy Auth with OAuth2 Proxy [with Nginx | with Traefik] Self-hosting SSO (Part 3): Keycloak + LDAP The dream There are plenty of great services to self-host, including Nextcloud, and Tandoor Recipes. If you've ever tried self…
Although you might assume that your server is already secure, there are some simple practices you should be following to harden your server. In the event of a compromise, these practices will allow you to limit the damage that can be done by attackers. Although this guide was written for Ubuntu Server 20.04 LTS (focal) this guide should be mostly transferable to other Linux distributions. 1. Get…
Why Netlify CMS? Netlify CMS is a headless CMS that makes it easy to write and edit content (e.g. markdown files) stored in a Git repository. It is easy to configure - you only need to update a YAML config file. It is a great choice when wanting to add content to any site built with a static site generator such as Next.js, Gatsby, Hugo, etc. As the project name suggests, the project was built with…
Unlike social network sites, this one is all mine. I am a software engineer by trade - in the coming months, you'll be able to find musings and various guides on assorted tech topics. For now, you're probably just wondering what to do first. Let me help get you going as quickly as possible. Find (and follow) me on my various online profiles below: My links Find me on StackExchange Find me on…